Ministry of Health Builds Vulnerability Analysis Tool
OpenKat is a vulnerability analysis tool developed by the Ministry of Health. BiteStreams has helped developed quality software and keep performance high.

The Goal
Automate the work of pentesters, with standardized reports and continuous scheduling and forensically secured, historical storage.

The Challenge
Managing historical data together with a materialized graph view. Keeping the system performant and stable while assuring proper developer experience.

The Approach
Creating an encrypted raw (meta-data) database and developing communication pipelines between the frontend, scheduler and workers.
- Sector
- Public Sector
- Use Case
- Application Monitoring

About OpenKat
During Covid, the Ministry of Health faced a number of unprecedented challenges. They became responsible for monitoring a lot of new internal systems, while connecting to several external parties. The high demand for robust penetration tests resulted in building an application that continuously scans and monitors these systems. Crucially, it reports its findings in a structured format. After 1.5 year of work, this tool – OpenKat – is now open source, since the first of July 2022.
Automated & Provable pentesting
The ministry of health faced several challenges in the automation of pentests, here we will point out a few of the most prominent ones.
- Every tool & pentest is different: Every pentest is different, because the finding of one vulnerability might lead to the finding of other vulnerabilities. Additionally, every pentester uses different tools (from the plethora of tools available), like nmap, shodan, and others, almost none of these output their results in a standard format.
- Pentesting over time: Another challenge is the fact that findings in the past should be related to the findings found at present, and these findings should be digitally proven, this mechanism allows one to create a form of accountability.
All in all these requirements resulted in a complex set of services that need to operate seamlessly to achieve the results that were aimed for. The security team had a handful of people working on these challenges, which produced a proof of concept of OpenKat. Challenges still present were the right conceptual architecture, structure and manpower. The team got the green light to build a proper MVP and was looking to expand its development capacity.
Solid foundations, data engineering & DevOps
Between April and July 2021, BiteStreams joined the OpenKat team. As the applications got more complex, we helped the team set up automated development environments, including CI/CD test and build pipelines with docker and github actions. These pipelines and efforts helped the team keep its fast pace and contributed with a much easier onboarding experience for the many people that joined the efforts of building OpenKat. Additionally, we built several security use cases and contributed to the architecture, data modelling and interface design of the application landscape.
Outcome
The project is still actively being built and maintained, and has got a lot of positive feedback from the community.
Example page: KAT-alogus
OpenKat provides a list of scanning tools in their so-called KAT-alogus:
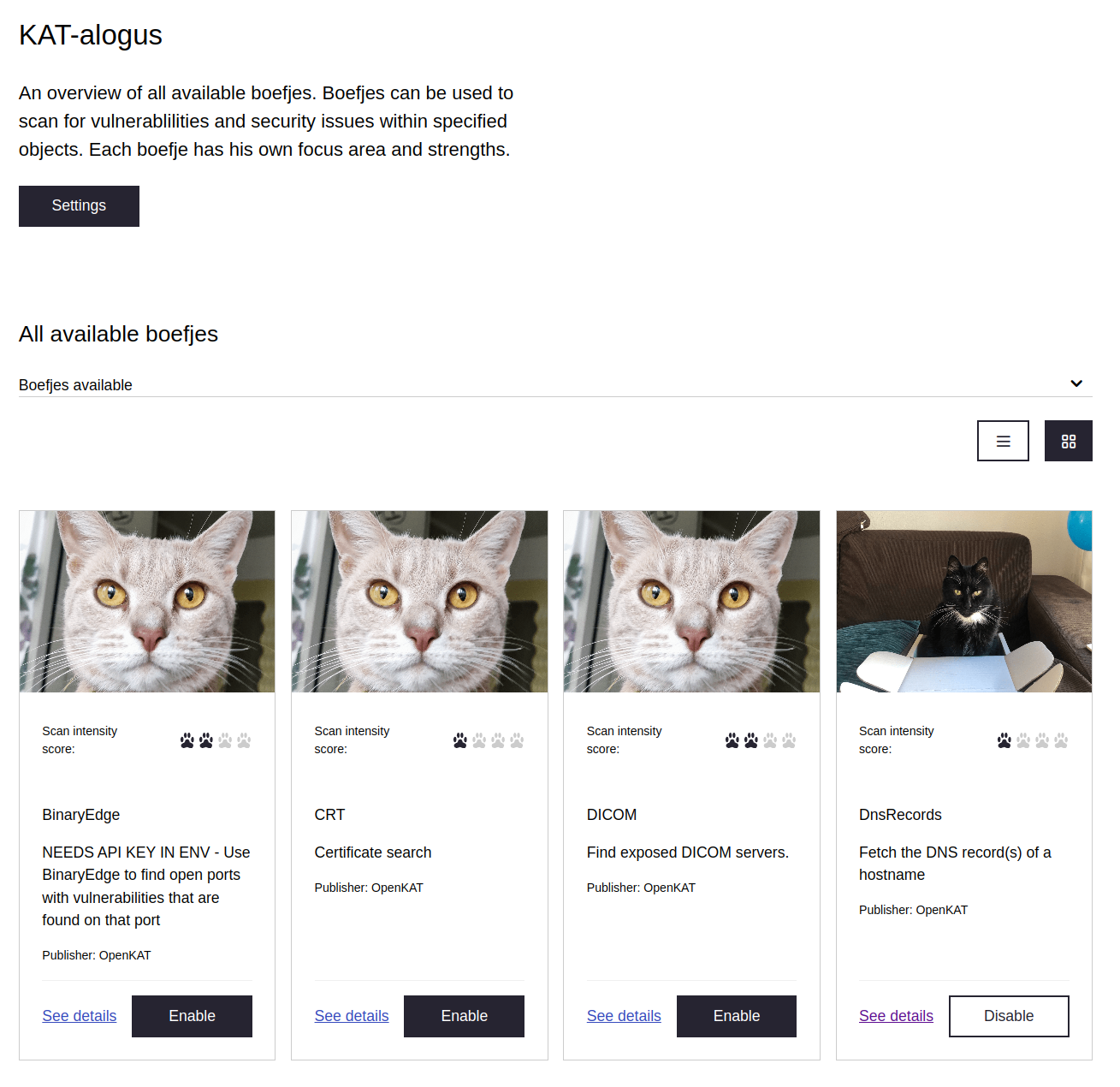
Objects are scanned with all enabled tools automatically
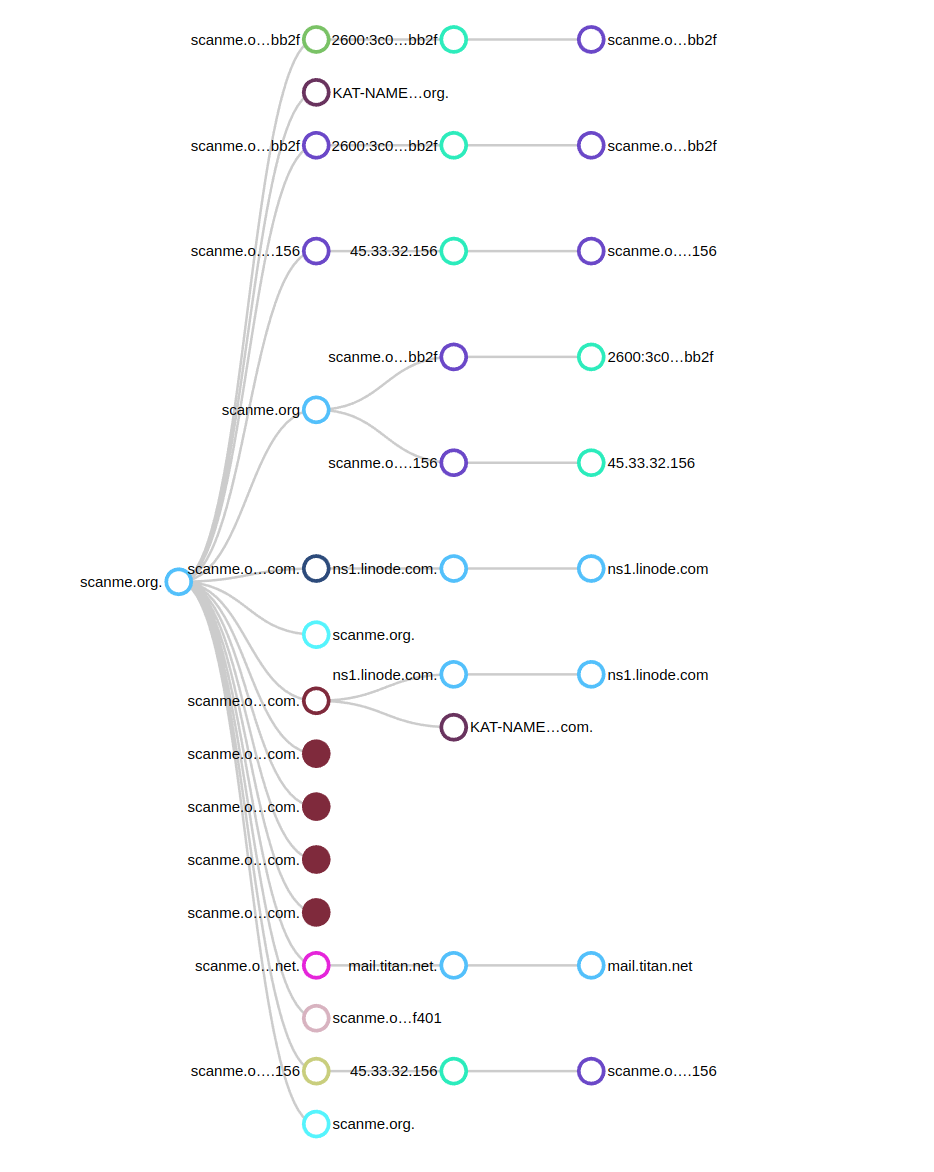
Example page: Object Graph
When adding - for example - https://scanme.org we let OpenKat run and automatically get the following object graph after we enable a DNS scanning tool:
At May Contain Hackers 2022 (MCH) a tent was set up for OpenKat specifically.
Features: